
What is a threat score?
In the world of cybersecurity and online services, an IP “threat score” (also sometimes called a “risk score” or “trust score”) is a simplified metric designed to quickly indicate the potential risk associated with a particular IP address.
Usually, this is a numerical value (for example, 0-100) or a categorical label (for example, low, medium, high, severe) generated by an IP intelligence provider. In fact, some providers’ entire business model is based on selling these scores to their customers.
The goal of such a score is to offer an at-a-glance assessment: is this IP address likely to be harmless, or could it be involved in malicious activities like spam, fraud, botnet operations, or other cyber threats?
The problems with threat scores
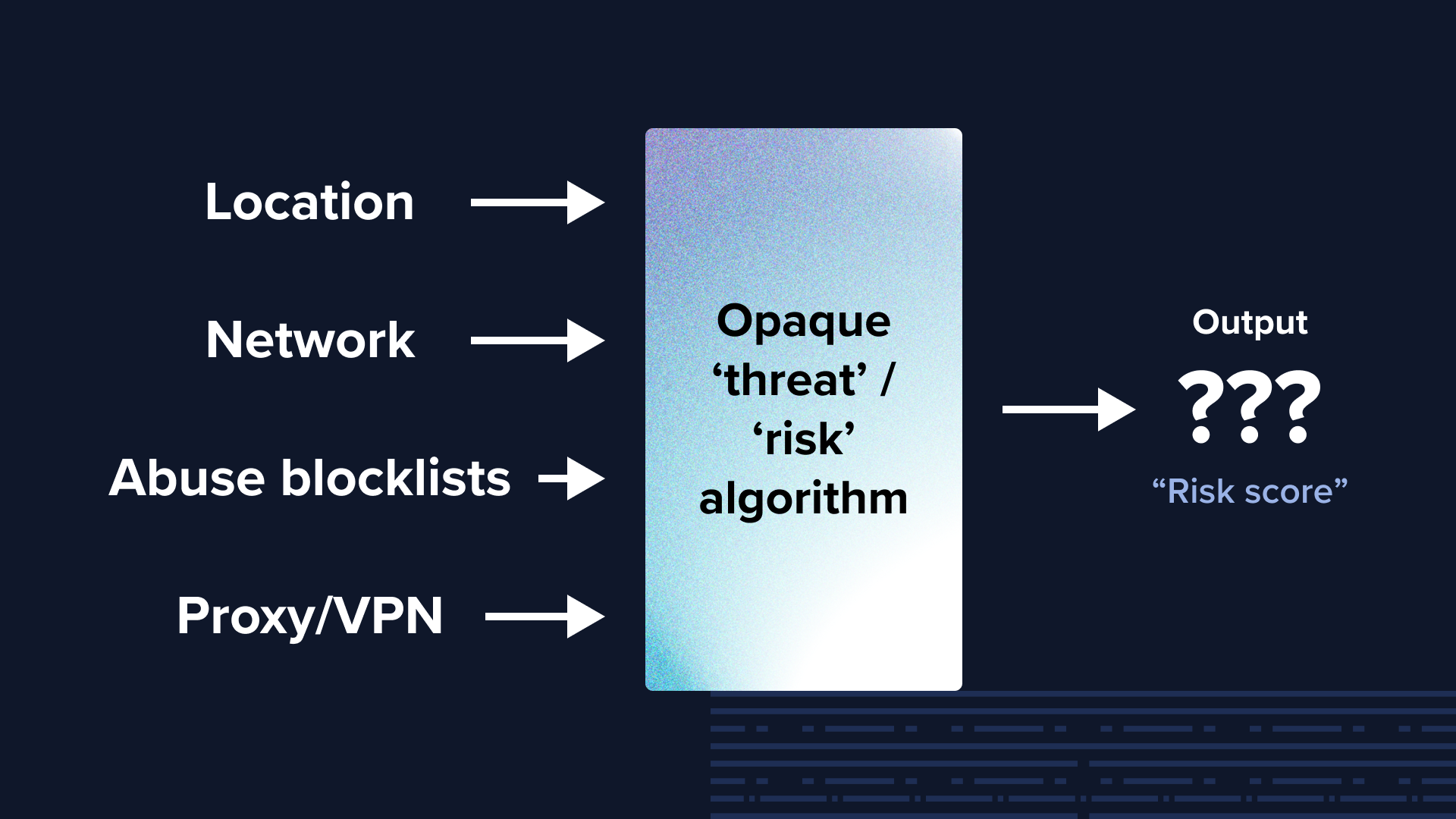
We get it. It's tempting to want a quick answer. But while convenient on the surface, we find that these scores are often opaque, impossible to decode, and don‘t reflect the reality of the threat landscape in 2025.
The “black box” problem: Lack of transparency and understanding
Most services offering a generic threat score don't fully disclose how that score is calculated. What specific data points are included? How are they weighted? What is the refresh rate of the underlying data contributing to the score?
This opacity makes it incredibly difficult to truly trust the score or troubleshoot why a particular IP was flagged (or not flagged). It’s like a magic eight ball: you get an answer, but you don’t know why.
One-size-fits-all doesn't fit anyone perfectly
Your business is unique. Your risk appetite is unique. The way different online behaviors impact your specific service is unique. A generic score, by its very nature, cannot cater to these individual nuances.
- For an e-commerce platform, a transaction from a VPN combined with a mismatched billing and shipping country might be a high-risk indicator.
- For a media streaming service, a user connecting via a VPN to protect their privacy might be perfectly acceptable, while an IP address associated with known credential stuffing tools is the real threat.
A single score applied universally often leads to suboptimal outcomes for everyone.
What we mean by “threat intelligence”: The IPLocate data points
At IPLocate, we take a fundamentally different approach. We believe that true, effective security comes from understanding the nuances of your traffic and making informed decisions based on rich, transparent data.
Our philosophy is built on providing the detailed, verifiable building blocks you need to construct a strong security posture.
We don't offer a pre-canned score because a single number can rarely capture the multifaceted nature of online interactions. Instead, we provide a comprehensive suite of data points about an IP address, allowing you to assess risk based on factors you define as critical.
Here are some of the key granular data points IPLocate offers and their implications for threat intelligence:
Privacy service detection
Understanding if a user is attempting to obscure their true IP address is often the first step in risk assessment.
- VPN detection: Virtual Private Networks are widely used for legitimate privacy reasons, but they are also a common tool for fraudsters, account takeovers, and circumventing geo-restrictions. Knowing an IP is a VPN allows you to apply appropriate scrutiny.
- Proxy detection: Similar to VPNs, various types of proxies (HTTP, SOCKS, etc.) can be used to mask an IP address. We help you identify these, distinguishing between, for example, residential proxies (often used in sophisticated fraud) and datacenter proxies.
- Tor (Dark web) exit node detection: The Tor network provides strong anonymity and is frequently associated with higher-risk activities due to its use in evading censorship and by malicious actors.
- Hosting provider detection: Identifying if an IP address originates from a data center or hosting provider (like AWS, Google Cloud, Azure, or smaller providers) is crucial. While many legitimate services run on cloud infrastructure, these IPs are also commonly used for botnets, automated attacks, fake sign-ups, and other forms of abuse.
Abuse and reputation data
- Threat intelligence feeds / Blocklist status: We monitor and integrate data from various reputable sources that track IPs involved in spam, malware distribution, phishing, and other abusive behaviors. Knowing if an IP is listed on such a feed is a strong indicator of potential risk.
Network context
The network an IP address belongs to provides invaluable context:
- ASN information: We provide the Autonomous System Number (ASN), the ASN's registered name, and importantly, the ASN type (for example, "Business," "Hosting," "Education," "ISP"). An IP address from an ASN categorized as "Hosting" might carry different risk implications for your use case than one from a "Business" or residential "ISP" ASN, especially when combined with other data points.
- Company information: Where available, we provide details about the company that owns the IP block, including its name, type, and domain. This can help differentiate, for instance, a corporate VPN from an IP address registered to a known server farm.
Precise geolocation data
- Country, region, city, latitude/longitude, timezone: While not a direct "threat" indicator in isolation, precise geolocation is a vital piece of the puzzle. You can use it to check for consistency with a user's stated location, identify connections from regions you don't serve, or flag transactions from areas with a high incidence of fraud relevant to your business.
A cornerstone of our service is the accuracy and timeliness of this data. The online landscape changes constantly, with IP address assignments and usage patterns shifting daily. We are committed to continuous updates to ensure the data you receive is as current and reliable as possible.
Practical examples: Using IPLocate data for custom risk logic
So how does this look in practice? Here are a few simplified examples of how you might combine IPLocate's granular data to build custom risk logic:
Scenario 1: E-commerce fraud prevention
Goal: Identify potentially fraudulent orders before processing.
IPLocate data used: VPN status, proxy status, Tor status, geolocation (country), ASN type, abuse blocklist status.
Example custom logic:
IF (IPLocate.privacy.is_vpn === true OR IPLocate.privacy.is_proxy === true OR IPLocate.privacy.is_tor === true)
AND IPLocate.country_code !== User.billing_country_code
AND (IPLocate.asn.type === 'hosting' OR IPLocate.is_on_abuse_list === true)
THEN
flag_order_for_manual_review OR increase_friction_SCA_challenge;
ELSE IF IPLocate.country_code === User.shipping_country_code
AND IPLocate.asn.type === 'isp'
AND IPLocate.privacy.is_vpn === false
THEN
assign_low_risk_to_transaction_ip_component;
Scenario 2: Preventing account takeover or credential stuffing
Goal: Detect suspicious login attempts.
IPLocate data used: Hosting provider status, Tor status, ASN type, geolocation (new or unusual city/country for the user).
Example custom logic:
IF (IPLocate.privacy.is_hosting === true OR IPLocate.privacy.is_tor === true)
AND (IPLocate.asn.type === 'hosting' OR IPLocate.asn.type === 'business') // Potentially from a compromised server
AND IP_is_new_to_user_account
THEN
trigger_multi_factor_authentication OR notify_user_of_suspicious_login_attempt;
Scenario 3: Content scraping or bot detection
Goal: Identify and block non-human traffic abusing your content or APIs.
IPLocate data used: Hosting provider status, ASN type, proxy status.
Example custom logic (combined with other signals like request velocity):
IF IPLocate.privacy.is_hosting === true
AND IPLocate.asn.type === 'hosting' // Common source of bots
AND User_Agent_is_suspicious OR request_velocity_is_high
THEN
serve_captcha OR temporarily_block_IP_from_resource;
These are just basic illustrations. The real power comes when you layer these IP intelligence signals with your own internal data about user behavior, transaction history, and other contextual information. You can assign weights to different IPLocate data points (for example, Tor exit node might be a higher risk indicator for you than a generic VPN) and create sophisticated, nuanced risk assessment models.
We're here to help you build your custom solution
At IPLocate, our commitment is to provide the most accurate, comprehensive, and up-to-date granular IP intelligence possible. We believe this is the best foundation for any modern security or fraud prevention system.
While we don't provide a one-size-fits-all score, we do provide support. We’d love to work with you to build a custom solution that meets your needs. Whether it's understanding the nuances of specific data fields or discussing strategies for combining them effectively, our team is available to assist. Get in touch.
We encourage you to explore our API documentation to see the full range of data we offer.


